While my CCNP studies are going well, this last week I have been setting up some more linux webservers at work, and I came across two issues. Both with simple solutions.
First was installing a SMTP relay server inside the network so websites (such as this one) can send admin emails. Before I had been using an external smtp server, in the case of this site it was google mail, and while this is great for a single personal site it is not really the way you want to have it set up. One of the main resons of course is that by having your own internal mail server, only that one machine needs to connect to the outside.
It is actualy very easy to set this up, simply installing postfix, giving it a very basic set up. Using unbuntu and aptitude there is even a simple walk through script to get these configurations in. Below is the default config you need to set up.
myhostname = host.domain.com
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = domain1.com, domin2.com, localhost
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128 192.168.0.0/24 172.16.0.0/16
mailbox_size_limit = 050000000
recipient_delimiter = +
inet_interfaces = all
inet_protocols = allThe important one is “mynetworks = …….”
This is telling postfix that it should act as a rely from any host in these ranges that tries to use it to send mail thought it. But once you have the set up above and as long as the servers are in the ip ranges configured then you are good to go.
Just note a few things! First this is not the most secure set up, any device in the ranges can now send internet mail, this could end up a potential method of attack where malicious software attempts to send spam. Either be very care full in securing what devices can use the relay server or else think about using authentication to secure it.
Secondly if you do not have a static IP, and your mail server does not have a correct public DNS record set up, you may find some companies will refuse to accept mail from it. This is quite a standard way to prevent them getting hit by spam (Zombi clients infected with malware generally don’t have DNS records set up, company mail servers do). So if you expect to be sending lots of mail to a wide variety of internet address so make sure you sort this out.
My next step in this is to extend postfix to not only be a relay for my webservers but to become a full blown email server that revives internet mail for my domains.
The other thing I came across was mod_proxy and mod_proxy_http, A while ago before I knew what I was doing I set up some websites on a server. Now looking back I realise that my first attempt was poor and I need to build a new server up and move the sites over. But with only one external IP to play with and multiply sites there is an issue of trying to keep every thing live and working during this process. The network looks something like below.
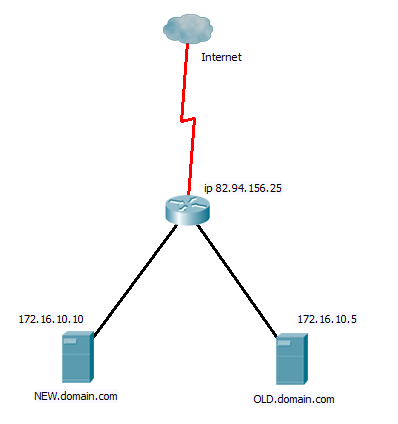 And on the old server I have the following virtual host file.
And on the old server I have the following virtual host file.
<VirtualHost * >
ServerName site1.domain.com
# Indexes + Directory Root.
#DirectoryIndex index.html
DocumentRoot /var/XXX/
<Directory /var/XXX/>
Options Indexes FollowSymLinks MultiViews
Options -Indexes
AllowOverride FileInfo
Order allow,deny
allow from all
</Directory>
</VirtualHost>
<VirtualHost * >
ServerName site2.domain.com
# Indexes + Directory Root.
#DirectoryIndex index.html
DocumentRoot /var/WWW/
<Directory /var/WWW/>
Options Indexes FollowSymLinks MultiViews
Options -Indexes
AllowOverride FileInfo
Order allow,deny
allow from all
</Directory>
</VirtualHost>So I set the first website up on my new server, but only having one external IP address, I can’t then easily forward external traffic to the new server. NAT/PAT wont work as all traffic is coming in on port 80. However the solution with mod_porxy_http is simple. Once I have set up the site on the new server and configured a virtual host for it. I can then update the virtual host file on the old server for the moved site to contain this entry.
<NameVirtualHost *
<VirtualHost *>
ServerName site1.domain.com
ProxyRequests Off
<Proxy *>
Order deny,allow
Allow from all
</Proxy>
ProxyPass / http://NEW.domain.com/
ProxyPassReverse / http://NEW.domain.com/
</VirtualHost>Now although the requests are still coming in to the old server it is simply passing them to the new server and relaying the replies back. We can carry on moving each site over in turn until all the old server is doing, is acting as a proxy for all the site that are now running on the new server. We can then update the NAT/PAT if we wish to point directly to the new server and decommission the old server.
Another reason you might want to employ Mod_proxy is if you have several heavily utilised sites that you want to run on separate hardware, but like this example you only have one public IP address. Having one physical box acting as a proxy server, you can farm out the requests to as many physical boxes as you wish. Taking this further and implementing the server load balancing that comes on many CISCO routers, along with a couple of low spec front end servers acting as proxy to your web-servers behind you can achieve, redundant, load balancing at low cost.
I have often found that set-ups that cost many 10’s thousands, can be emulated with hardware that is often already on site, and a little careful thought.
But that’s been my week so far, fun stuff 🙂
DevilWAH
